Saturday, 21 December 2019
VERIFICATION OF SUCESSFULL INSTALLATION AND CONFIGURATION OF AD CONNECT
STEP 1 -Verifying in Azure AD Portal:
Log into Azure AD portal with Global Admin Credentials
In the home page click Azure Active directory => AD Connect in the left blade
Check Sync Status and Last sync timings
STEP 2 – checking through PowerShell:
Log into PowerShell in the AD Connect server with elevated rights,
Run Get-ADSyncScheduler
The Value of “SyncCycleEnabled” has to be “True”
SAMPLE:
STEP 3 – checking User profiles:
Log into Portal.azure.com with GA credentials
Azure Active Directory => Users
You should be able to see users with Source as Windows server AD.
run, (Get-ADSyncGlobalSettings).Parameters | Select Name,Value
in powershell with elevated rights. The above command will give you the details of your company`s Ad Connect configurations. It also has AD Connect version.Alternatively you can check from Control panel.
Log into Azure AD portal with Global Admin Credentials
In the home page click Azure Active directory => AD Connect in the left blade
Check Sync Status and Last sync timings
STEP 2 – checking through PowerShell:
Log into PowerShell in the AD Connect server with elevated rights,
Run Get-ADSyncScheduler
The Value of “SyncCycleEnabled” has to be “True”
SAMPLE:
PS C:\Windows\system32> get-Adsyncscheduler
AllowedSyncCycleInterval : 00:30:00
CurrentlyEffectiveSyncCycleInterval : 00:30:00
CustomizedSyncCycleInterval :
NextSyncCyclePolicyType : Delta
NextSyncCycleStartTimeInUTC : 12/19/2019 1:00:20 PM
PurgeRunHistoryInterval : 7.00:00:00
SyncCycleEnabled : True
MaintenanceEnabled : True
StagingModeEnabled : True
SchedulerSuspended : False
SyncCycleInProgress : False
STEP 3 – checking User profiles:
Log into Portal.azure.com with GA credentials
Azure Active Directory => Users
You should be able to see users with Source as Windows server AD.
run, (Get-ADSyncGlobalSettings).Parameters | Select Name,Value
in powershell with elevated rights. The above command will give you the details of your company`s Ad Connect configurations. It also has AD Connect version.Alternatively you can check from Control panel.
PS C:\Windows\system32> (Get-ADSyncGlobalSettings).Parameters | select Name,Value
Name Value
---- -----
Microsoft.Synchronize.SynchronizationPolicy Delta
Microsoft.Synchronize.StagingMode True
Microsoft.SynchronizationOption.JoinCriteria AlwaysProvision
Microsoft.UserSignIn.DesktopSsoEnabled False
Microsoft.Synchronize.MaintenanceEnabled True
Microsoft.OptionalFeature.ExportDeletionThresholdValue 500
Microsoft.Version.SynchronizationRuleImmutableTag V1
Microsoft.SynchronizationOption.AnchorAttribute mS-DS-ConsistencyGuid
Microsoft.OptionalFeature.DirectoryExtensionAttributes
Microsoft.OptionalFeature.FilterAAD False
Microsoft.GroupWriteBack.Forest
Microsoft.GroupWriteBack.Container
Microsoft.SynchronizationOption.UPNAttribute userPrincipalName
Microsoft.Synchronize.SchedulerSuspended False
Microsoft.OptionalFeature.DirectoryExtension False
Microsoft.SynchronizationOption.CustomAttribute
Microsoft.Synchronize.TimeInterval 00:30:00
Microsoft.Synchronize.ServerConfigurationVersion 1.4.32.0
Microsoft.SystemInformation.MachineRole RoleMemberServer
Microsoft.AADFilter.AttributeExclusionList
Microsoft.OptionalFeature.DeviceWriteBack False
Microsoft.OptionalFeature.AutoUpgradeState Suspended
Microsoft.Synchronize.NextStartTime Thu, 19 Dec 2019 13:00:20 GMT
Microsoft.Synchronize.RunHistoryPurgeInterval 7.00:00:00
Microsoft.OptionalFeature.GroupFiltering False
Microsoft.ConnectDirectories.WizardDirectoryMode AD
Microsoft.Synchronize.SynchronizationSchedule True
Microsoft.OptionalFeature.ExchangeMailPublicFolder False
Microsoft.OptionalFeature.UserWriteBack False
Microsoft.OptionalFeature.ExportDeletionThreshold True
Microsoft.DeviceWriteBack.Forest
Microsoft.OptionalFeature.DeviceWriteUp True
Microsoft.OptionalFeature.HybridExchange False
Microsoft.AADFilter.ApplicationList
Microsoft.DirectoryExtension.SourceTargetAttributesMap
Microsoft.UserWriteBack.Forest
Microsoft.DeviceWriteBack.Container
Microsoft.UserWriteBack.Container
Microsoft.UserSignIn.SignOnMethod PasswordHashSync
Microsoft.OptionalFeature.GroupWriteBack False
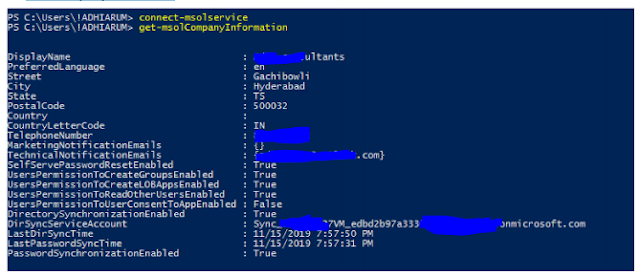
Connect-msolservice // connect to Ms online service , use Global Admin credentials
Get-MsolCompanyInformation
gives info about last sync cycle, password syn enabled or not etc
Friday, 22 February 2019
Auto Cert Rollover in ADFS and setting the new token signing as primary and changing the old one as secondary | Renew federation certificates for Office 365 and Azure Active Directory
Auto Cert Rollover in ADFS and setting the new token signing as primary and changing the old one as secondary
If you get a token signing certificate when the old certificate is expiring, the new certificate will sitting only as "secondary" until the promotion threshold is met .
you cannot change the cert as Primary. It will be grayed out.
Step 1: Check the AutoCertificateRollover state
get into the Primary ADFS server
run Get-Adfsproperties in PowerShell with elevated rights.
check if autocertificateRollover is set to "true"
here the threshold is 5 days so the new certificate will become as Primary 5 days before the expiry of the original certificate.
Step 2: Confirm that AD FS and Azure AD are in sync
Install-Module MSOnline
Connect to Azure AD using the MSOnline PowerShell-Module.Import-Module MSOnlineConnect-MsolService
Check the certificates configured in AD FS and Azure AD trust properties for the specified domain.Get-MsolFederationProperty -DomainName <domain.name> | FL Source, TokenSigningCertificate
If the thumbprints in both the outputs match, your certificates are in sync with Azure AD.
if not run Update-MSOLFederatedDomain –DomainName <domain>
Renew the token signing certificate automatically (recommended)
You don't need to perform any manual steps if both of the following are true:You have deployed Web Application Proxy, which can enable access to the federation metadata from the extranet.You are using the AD FS default configuration (AutoCertificateRollover is enabled).Check the following to confirm that the certificate can be automatically updated.
1. The AD FS property AutoCertificateRollover must be set to True. This indicates that AD FS will automatically generate new token signing and token decryption certificates, before the old ones expire.
2. The AD FS federation metadata is publicly accessible. Check that your federation metadata is publicly accessible by navigating to the following URL from a computer on the public internet (off of the corporate network):https://(your_FS_name)/federationmetadata/2007-06/federationmetadata.xmlwhere (your_FS_name)is replaced with the federation service host name your organization uses, such as fs.contoso.com. If you are able to verify both of these settings successfully, you do not have to do anything else.
Example: https://fs.contoso.com/federationmetadata/2007-06/federationmetadata.xml
REFER:
https://blogs.msdn.microsoft.com/vilath/2015/09/02/how-to-update-certificates-for-ad-fs-3-0/
Thursday, 21 February 2019
How to delete a managed Domain in Azure.
How to delete a managed Domain in Azure.
Some time we might be in a need to delete the
managed domain in Azure. Follow the below mentioned steps to delete the
managed Domain or custom Domain. However you will not be able to delete the Primary domain (abc.onmicrosoft.com) as it is the name of your directory abc.onmicrosoft.com).
- Log in to Portal.azure.com with global Admin credentials
- Azure
Active Directory => Custom Domain names
- Click on
the custom domain name => Click Delete
To delete a custom domain name, you must first ensure that
no resources in your directory rely on the domain name.
You can’t delete a domain name from your directory if:
- · Any user has a user name, email address, or proxy address that includes the domain name.
- · Any group has an email address or proxy address that includes the domain name.
- · Any application in your Azure AD has an app ID URI that includes the domain name.
You must change or delete any such resource in your Azure AD
directory before you can delete the custom domain name.
-
Refer the docs for more info.
Getting error in ADFS proxy 2.0 "Encountered error during federation passive request"
Some customers who are using 2008 server for ADFs proxy may sometime get errors
"Encountered error during federation passive request"
This usually happens when they change the certificate which is about to expire.
Usually for this kind of issue where the ADFS service and metadata when not accessible extenally we check for certificate bindings
we will be going to PowerShell with admin rights
run
get-Webapplicationproxysslcertificate
compare the thumbprint with ADFS
but in 2008 R2 we don't have this option to run PS command
so run the ADFS proxy 2.0 wizard that will be fixing the most of the issues.
"Encountered error during federation passive request"
This usually happens when they change the certificate which is about to expire.
Usually for this kind of issue where the ADFS service and metadata when not accessible extenally we check for certificate bindings
we will be going to PowerShell with admin rights
run
get-Webapplicationproxysslcertificate
compare the thumbprint with ADFS
but in 2008 R2 we don't have this option to run PS command
so run the ADFS proxy 2.0 wizard that will be fixing the most of the issues.
Friday, 15 February 2019
Azure MFA Unexpected-Failed Result - MFA App Password calls being rejected with bad username/password
My users that use App passwords for the native mail client are not getting mail.
there has been many customers that are saying app passwords are not working with azure.
The back end team has fixed the issue. If you still have problem create a support ticket in Azure portal.
Subscribe to:
Comments (Atom)
வாழ்க்கை முழுவதைம் அள்ளிச்சென்ற பின், கனவில் மட்டும் வந்து ஏன் இன்பம் காட்டுகிறாய்... கனவு கலைந்ததும் உண்மை வாட்டுகிறது... கனவாவத...
-
Renew federation certificates for Office 365 and Azure Active Directory Auto Cert Rollover in ADFS and setting the new token signing as...
-
How to create an Azure AD or Azure Tenant First create a outlook account Sign in with that account Reach this URL to name your t...
-
Insufficient access rights to perform the operation error in Azure AD Connect are you're getting Insufficient access rights to perf...